Zero Trust Architecture (ZTA) is fast becoming the security model of choice as businesses worldwide recognize the need to better protect their networks and assets in light of today’s growing remote workforce.
By Anthony DeCristofaro
Special to the Financial Independence Hub
For many organizations, remote work began as a pandemic-induced novelty. More than a year later, however, it has become the new normal. Even when the world officially reopens, a large number of employees who have experienced the perks of working from home will no doubt be requesting the flexibility to continue doing so – that is, if their employers actually plan on transitioning back to a physical workplace.
Remote work presents new data security challenges: even for top-notch VPN
Granted, a reliable VPN will substantially lower your chances of being hacked. However, as the past year has shown us, even the most highly rated VPNs are far from foolproof. While they’ve always had their fair share of vulnerabilities (thus the need for constant updating), VPNs have been under constant assault since the pandemic began.
For example, one extremely sophisticated attack compromised more than 900 Pulse Secure enterprise VPN servers enabling the attackers to gain access, steal account credentials, and exfiltrate other sensitive data belonging to victim organizations.
The more employees using your VPN, the greater your network’s vulnerability
Pre-COVID, you had maybe 10% of employees using your VPN one or two days a week. Now, you likely have 90% of employees or more using your VPN five days a week. Each one of these employees creates a new point of vulnerability.
Your VPN can’t protect remote workers from malicious cyber activity. If just one compromised employee uses your VPN, you could soon have yourself an intruder. It’s a company’s worst nightmare and an attacker’s dream come true.
Zero Trust Architecture (ZTA) is the way forward
According to Gartner IT Research, “by 2022, 80% of new digital business applications opened up to ecosystem partners will be accessed through zero trust network access,” and 60% of enterprises will transition most of their remote access VPN solutions to ZTNA by 2023.
Unlike VPNs, platforms that operate with Zero Trust Architecture (ZTA) assume that security breaches happen – and rightly so. Take the recent Colonial Pipeline incident.
In May 2021, the fuel operator responsible for carrying 2.5 million barrels of fuel per day was temporarily shut down after being held for ransom by cybercriminals. This, combined with similar cyberattacks on SolarWinds, Microsoft Exchange, and others, prompted The White House to issue an Executive Order in support of a zero trust approach to security.
Biden’s recent order to transition the US government from VPN to zero trust is reinforcing the latter as the gold standard in security and promises to change the trajectory of network security across the globe.
The concept of Zero Trust Architecture (ZTA) is simple
No user or machine within or beyond your firewall should ever be trusted.
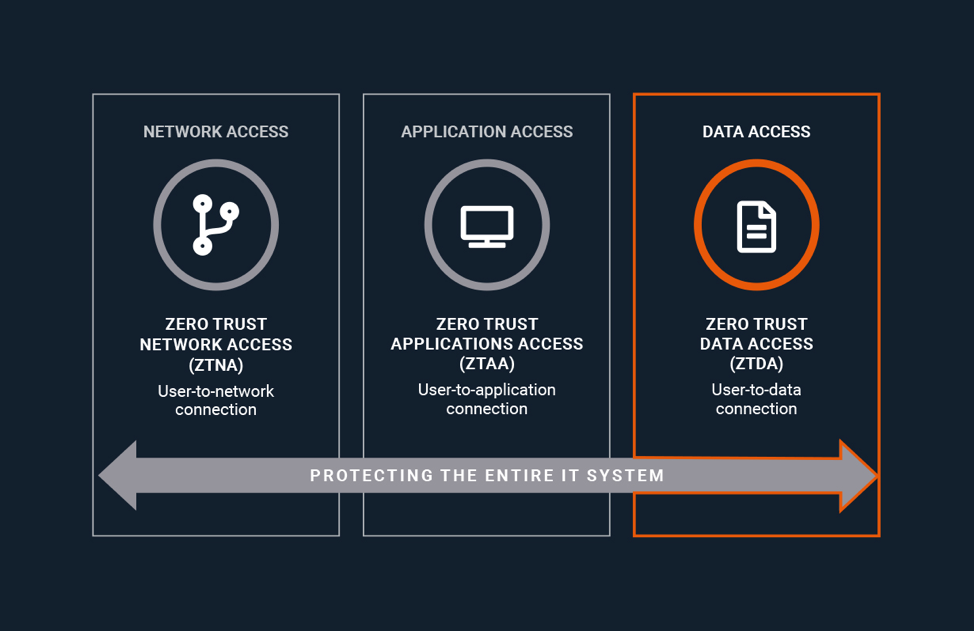
Unlike VPNs, which typically grant users access to large portions of infrastructure, Zero Trust Architecture (ZTA) platforms like Zero Trust Network Access (ZTNA) and Zero Trust Application Access (ZTAA) require user verification each and every time access is requested. This ensures individuals can only gain access to the assets and applications they need. As an added measure of security, all access attempts and actions (e.g. editing, copying, moving, and downloading) are tracked.
Like users, devices must also be authorized, and any device trying to access your network is automatically monitored in real-time. By permitting neither users nor devices to access your infrastructure freely, your organization’s sensitive assets are better protected.
How does Zero Trust Architecture (ZTA) limit network and application access?
It uses a process called micro-segmentation. This security technique provides granular segmentation to applications and workloads. Once applications and workloads have been micro-segmented, your IT administrator creates permissions policies to control which individuals and groups are allowed access to which segments.
An employee who is granted access to one segment doesn’t automatically gain access to other segments. Furthermore, access to the permitted segment is only granted after verification and authorization upon each and every request.
Is securing your network and applications with Zero Trust Architecture (ZTA) enough?
It’s a start.
However, stopping here discards the importance of protecting your organization’s greatest asset: your crown jewels, otherwise known as data.
When malicious attackers gain access to, say, your customer profiles or data around operations and intellectual property, they strike gold.
To protect your entire organization, you need to do more than secure your network and application access; you need to secure your data. At the moment, there is only one platform available worldwide that is capable of helping you accomplish this: FileFlex Enterprise Zero Trust Data Access (ZTDA).
Zero trust is about “verifying, every step of the way, how people access data, whether it’s through an application or device,” says Forrester Research analyst Steve Turner. FileFlex Enterprise is the data piece that zero trust has been missing.
In the same way that ZTNA and ZTAA applications are Zero Trust Architectures (ZTA) that use micro-segmentation to create secure connections between users, your network, and applications, Zero Trust Data Access (ZTDA) uses Zero Trust Architecture (ZTA) micro-segmentation to secure the connection between users and your data.
Whenever a request for data is received, secure zero trust data access processes kick in, providing secure, micro-level data access (as granular as a single file) that protects unauthorized access to your organization’s infrastructure.
You get to control precisely how narrow you make each individual user’s trust zone. You can also revoke access by user or on a file-by-file basis at any time. This means that, in the unlikely event attackers manage to make their way into your network, they are unable to move laterally, thereby minimizing damage.
Thanks to double encryption, all data transmitted undergoes end-to-end encryption. And because a connector agent is responsible for fulfilling all requests, users can’t intercept data at the server level. Think of it this way: when you go to the bank, you don’t help yourself to cash; the bank teller gets it for you. In the case of Zero Trust Architecture (ZTA), the bank teller is your organization’s connector agent.
Zero Trust Architecture (ZTA) is now being adopted by the US Department of Defence
That’s how secure it is.
The ideal zero trust solution should be built from the ground up to apply Zero Trust Architecture (ZTA) to networks, applications, and data. FileFlex Enterprise is the only data security solution of its kind and the most comprehensive platform for organizations that are ready to up-level their security around remote access to files and folders from the old-school perimeter-based model to zero trust.
Remote work is here to stay
Adversaries know this and they’re looking for ways to exploit any and all security vulnerabilities. Pivoting to a security infrastructure or enhancing your existing Zero Trust Architecture (ZTA) initiatives to facilitate fast, secure, and collaborative sharing is the smartest step you can take towards protecting your organization going forward.
 Anthony DeCristofaro trusts no one. As president and CEO of cybersecurity disruptor Qnext Corp., he is at the forefront of Zero Trust Data Access (ZTDA), the “heavy lifter” and transformative subset of Zero Trust Architecture (ZTA) that has become, thanks to President Biden’s new executive orders in support of a Zero Trust approach to security, the rising star in large-scale enterprise data protection and safety for the new remote workplace.
Anthony DeCristofaro trusts no one. As president and CEO of cybersecurity disruptor Qnext Corp., he is at the forefront of Zero Trust Data Access (ZTDA), the “heavy lifter” and transformative subset of Zero Trust Architecture (ZTA) that has become, thanks to President Biden’s new executive orders in support of a Zero Trust approach to security, the rising star in large-scale enterprise data protection and safety for the new remote workplace.
With an international business and technology background, DeCristofaro has been building disruptive technologies into best-in-category companies for more than 30 years. A major force in launching new and established tech players, DeCristofaro’s accomplishments include re-shaping the traditional photography landscape as CEO and co-founder of the Intel-invested MGI Software with PhotoSuite, the number one consumer digital photography product, outselling Adobe, and Microsoft, as well as VideoWave, a pioneer in the consumer video editing market. DeCristofaro steered MGI’s cap value on the TSE to over $1 billion, and later merged with Roxio in 2002.
He built his corporate career by setting up NEC Canada, and was behind the computer, notebook and monitor manufacturer’s entry into the market, propelling it to over $100 million in sales in its first year. As GM of AST Canada in the late ‘90s, his sales and marketing strategies drove sales from $2 million to over $400 million in just three years, representing 20 percent of AST’s global sales. Before joining Qnext, DeCristofaro ran his own tech start-up, iseemedia Inc., a mobile software company focused on bringing desktop email to cell phones via text with an advanced content delivery platform, acquired by Synchronica, a London Stock Exchange-listed listed company.